Security 225
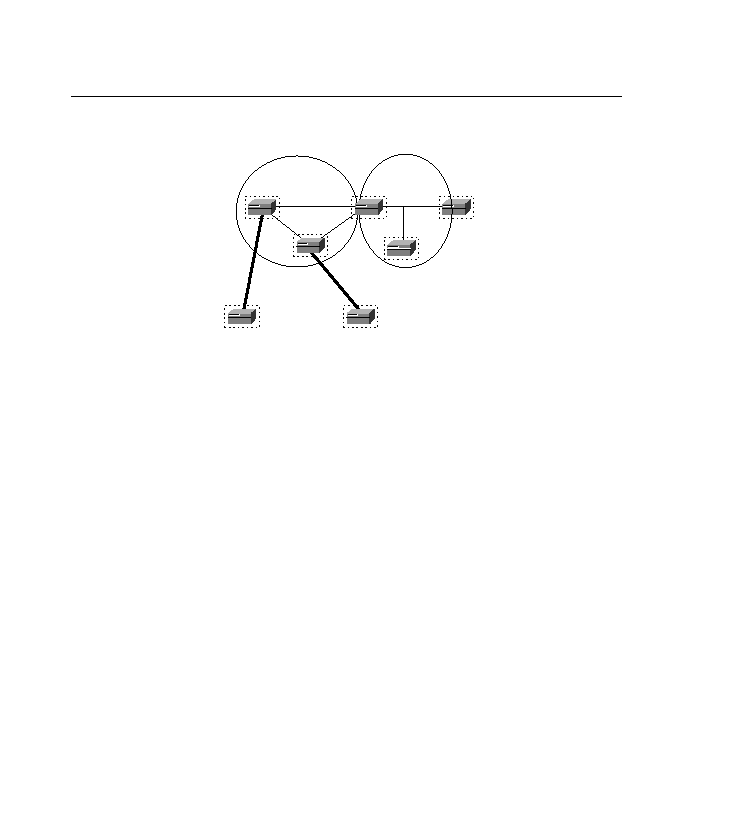
Figure 7-5
OSPF External Route Summarization
Scalable OSPF Internetworks
To design a scalable OSPF internetwork, make sure that the network conforms to the following:
·
Has no more than six hops from source to destination
·
Contains no more than 50 routers per area
·
Connects all areas to Area 0
·
Does not allow more than two areas per ABR
·
Uses totally stubby areas
·
Maximizes summarization
·
Uses multiple-path redundancy instead of virtual links
·
Does not overtax router memory
·
Has available bandwidth
Security
OSPF protocol exchanges between adjacent routers can be configured to use authentication.
Authentication provides added security for the routers that are on the network. Routers that do
not have the password will not be able to gain access to the routing information because
authentication failure prevents a router from forming adjacencies.
By default, routers use null authentication. Clear-text and Message Digest (MD5)
authentication can be configured. The rules of implementing security for OSPF are simple. All
routers in an area must have the same authentication key to form a neighbor and adjacency.
Area 1
RTA
128.213.64Р95
255.255.255.0
Area 0
RTB
RTC
RTD
BGP
BGP
128.213.96Р127
255.255.255.0
87200333.book Page 225 Wednesday, August 22, 2001 2:37 PM
