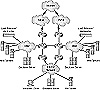
FIGURE 11.2 A complex firewall deployment
| Previous | Table of Contents | Next |
In order to contrast the potential complexity of a firewall deployment, refer to Figure 11.2. In this diagram, the firewall policy is distributed across a wide array of devices and includes dual ISP connections, dual DMZs (demilitarized zones—a concept of no man’s land taken from the warfare arena), connections to internal resources, Web server redirection and redistribution, and internal connectivity.

FIGURE 11.2 A complex firewall deployment
In their purest sense, DMZs do not have implied trust for any organization—all resources are suspect. A bastion host would be found in the DMZ. You may note that Figure 11.2 includes redirectors and redistribution resources, devices that help scale the Web server farm to support millions of connections. Most designers today must consider the inclusion of these resources in their designs, although this information is beyond the scope of the exam. Redirectors serve a single uniform resource locator (URL) and redirect users to one of many servers. This provides a simple load-balancing mechanism.
 | It may not be readily apparent, but the security offered by the network in Figure 11.2 is poor at best. The illustration is not intended to show a good design, but rather one that uses various components. |
There is more to implementing a security policy than purchasing and installing a firewall, even if the deployment is limited to this single mechanism. The implementation needs to include the policy itself, the acquisition and configuration of the various components, and installation, testing, and auditing.
An effective security policy, which provides a road map for the actual security deployment, should include the following elements:
It may be appropriate to hire a dedicated specialist to address your firm’s security needs. This person may be an employee reassigned from another position, a new hire, or a consultant. Consultants may yield the cheapest deployment given their experience with different organizations and equipment. If you hire a consultant, make sure that they warrant the trust that your firm will be placing in them and that everything they do is documented. It is always a good idea to conduct a thorough background review, as well as to check references. Non-disclosure agreements are also helpful, though it may be difficult to provide sufficient legal proof of breach for this to fully protect the organization.
 | Always have a second person trained on the security systems and technology. People leave jobs and fall ill—either way, there will be a lack of support. |
The best security plans include an auditable and verifiable component. It is one thing to prevent the attack in the first place, but if the administrator cannot ascertain that all attacks have been unsuccessful, there is a significant risk to the corporation.
Logging is one of the best methods for capturing the techniques used in an attack and for determining which resources were compromised. However, administrators must realize that truly skilled hackers can easily hide their activity or purge the logs if they are improperly stored. Thus, logs should always be written to a separate system with another layer of security between devices.
 | Logs should always be written to a secure server other than to the firewall itself. Once the firewall is compromised, a hacker can easily purge the log files, which are the best form of documentation for criminal prosecution. |
Remember Winnie-the-Pooh? He was a stuffed bear that came to life and, like most bears, loved honey. One of many themes in the Pooh stories was Winnie getting stuck because of his love of honey; one tale had his arm trapped in a honey pot, a vessel with a small opening used for storing honey.
Well, in the network security arena, honey pots build upon this very idea: Attackers want the honey, and they may get trapped if they try to obtain it.
Basically, the honey pot is a special fictional system designed to appear like the corporate data being sought—and designed to be hacked. Once an attack is detected by the firewall, the system redirects the session to the fictional data and invokes additional logging to capture information regarding the attack and the hacker.
| Previous | Table of Contents | Next |