626 Chapter 8: WAN Protocols and Design
Answers to Scenarios
Answers to Scenario 8-1: Point-to-Point Verification
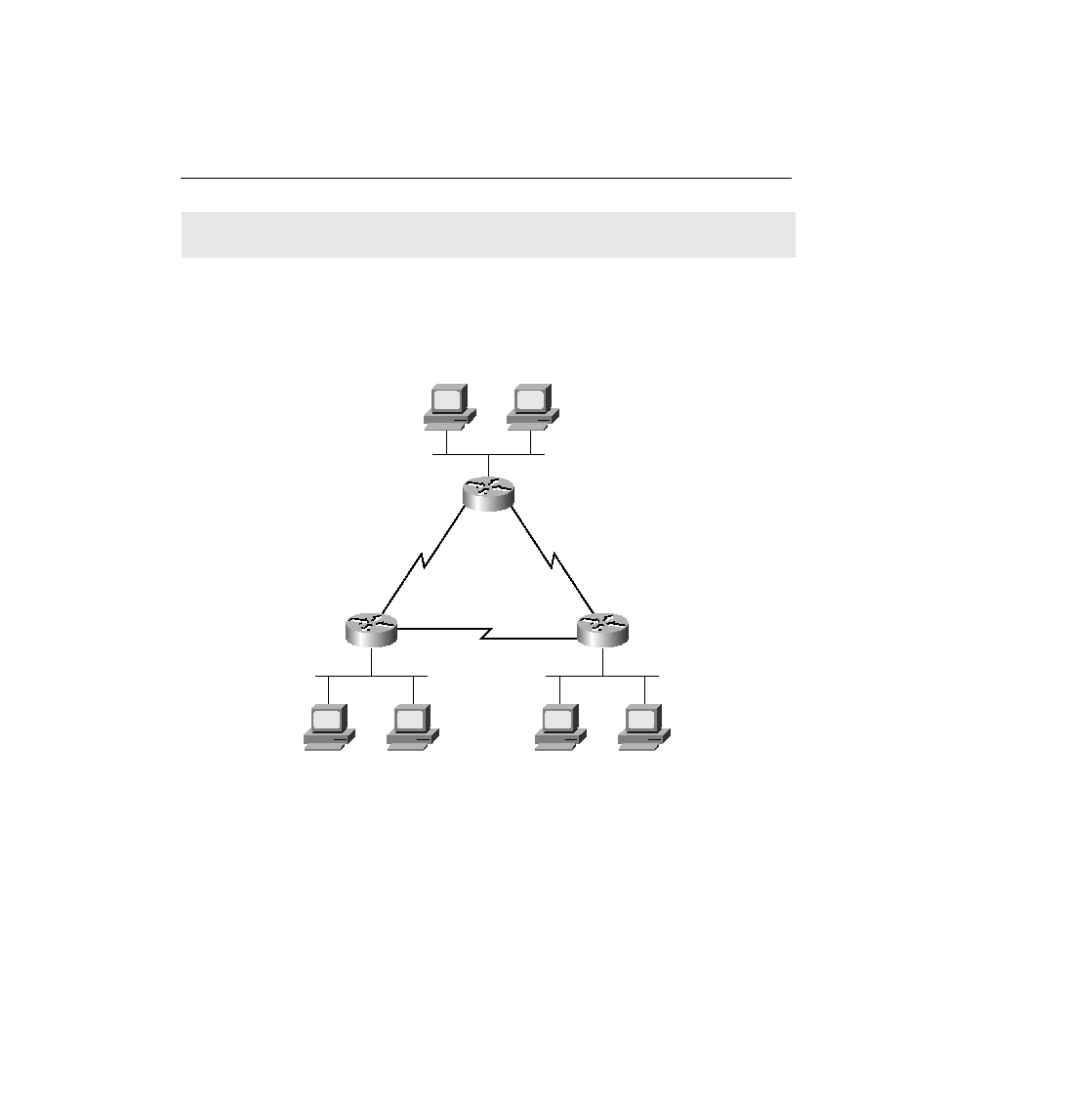
Figure 8-41 is a diagram that matches the configuration.
Figure 8-41
Sample Cartoon Network
The IP and IPX addresses used on the various router interfaces were one of the tasks for this
scenario. Table 8-53 is a completed version of Table 8-47, which was the blank table in which
you recorded your answers for this task. Finding all the IP and IPX addresses in Examples
8-33, 8-34, and 8-35 requires some persistence. The best plan of attack is to find all IP addresses
and masks that you can, then find all IPX network numbers, and finally decide which addresses
are in the same IP subnet and IPX network.
The full IPX addresses are a little more difficult to find. The best method with the commands
shown is via the show ipx interface brief command and the show ipx route command. In
particular, the routing table lists the full IPX addresses, not just the network numbers.
Albuquerque
subnet 199.1.1.32
Yosemite
Bugs
Daffy
s0
s1
.34
.33
.29
.193
.65
.66
.67
subnet 64
IPX net 1002
128
192
IPX net 1001
2001
2003
IPX net 2002
.130
.161
160
.35
s0
s1
.162
s1
Sam
Emma
Seville
.97
.98
.99
subnet 96
IPX net 1003
.194
s0
Elmer
Red
IPX net
subnet
subnet
subnet
IPX net
ch08.fm Page 626 Monday, March 20, 2000 5:17 PM
