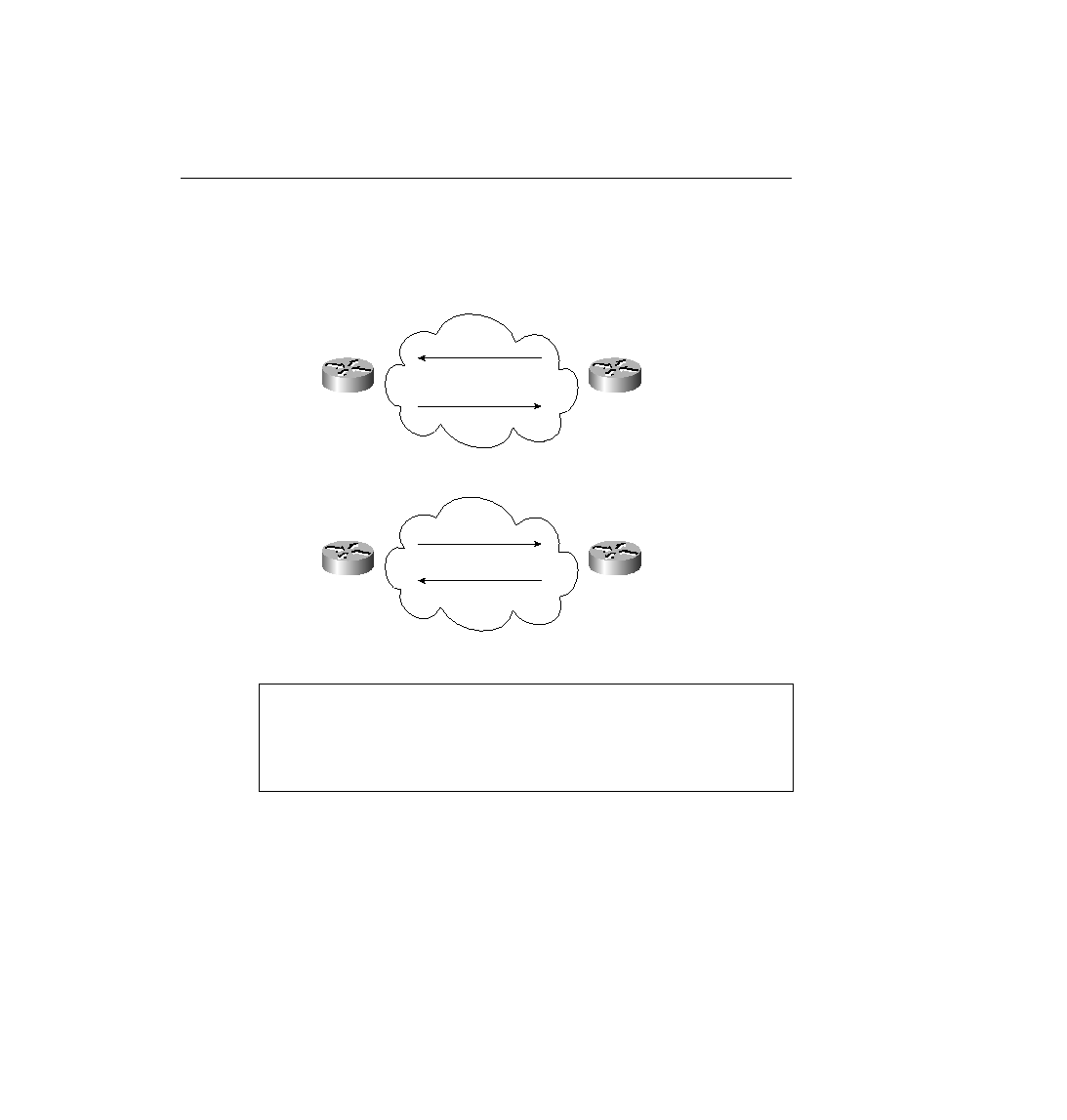
environments. Example 8-25 shows the CHAP configuration for Figure 8-26.
in CHAP flows, unless overridden by configuration. Each codes the same password. When
Router Barney receives a challenge from Router Fred, Router Barney sends an encrypted value,
which is the value Fred should compute given the name Barney, the password Bedrock, and the
original random number. CHAP authentication is completed if the two values match.
username Barney password Bedrock username Fred password Bedrock
! !
Interface serial 0 Interface serial 0
encapsulation ppp encapsulation ppp
ppp authentication chap ppp authentication chap
. .
Router
Router