Filtering IPX Traffic and SAPs 479
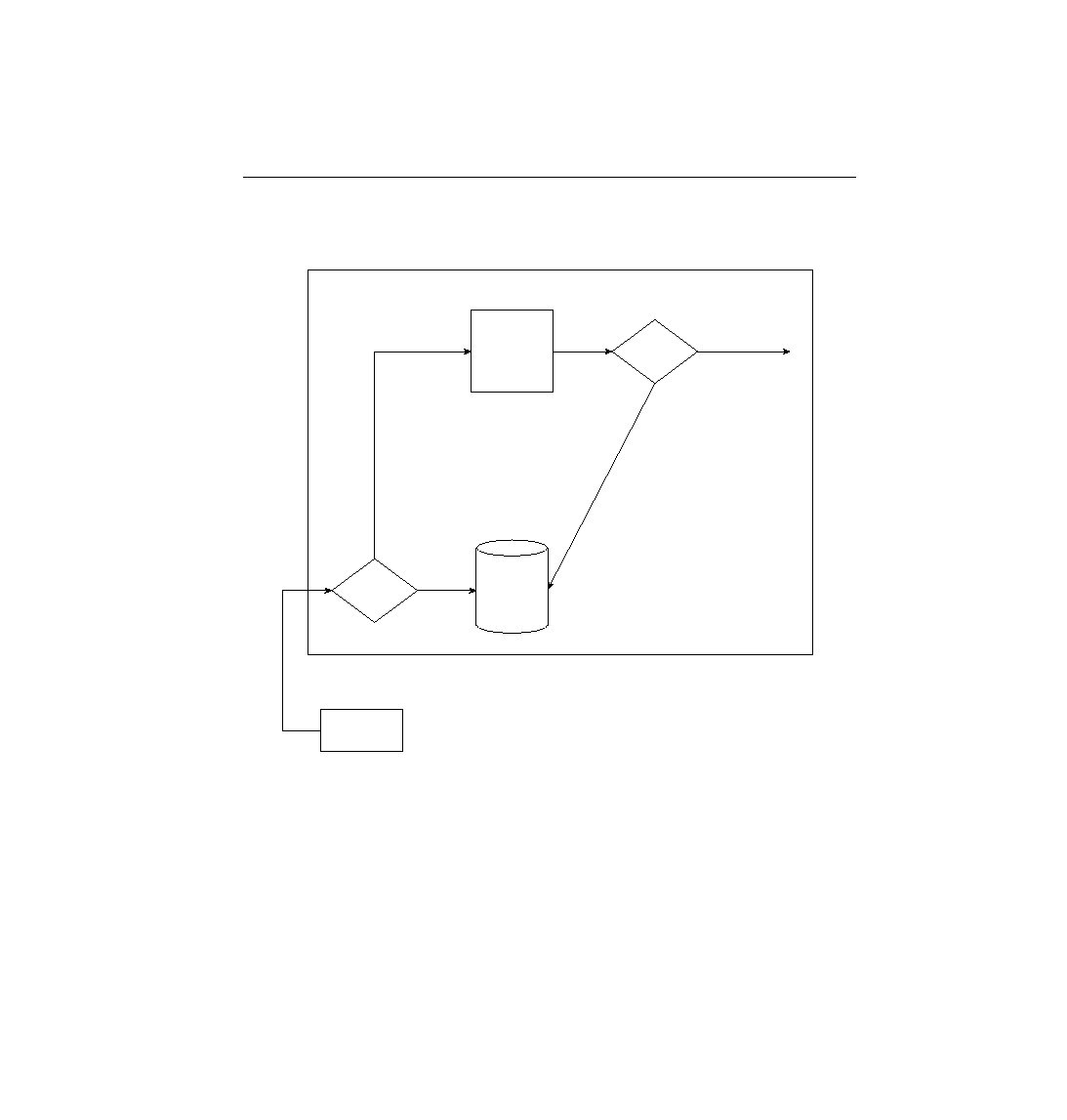
Figure 7-6
Locations Where Access List Logic Can Be Applied
The logic for access lists is true whether using standard or extended access lists. The only
difference is that extended access lists include more comparisons to determine a match. These
differences are outlined in the next few sections on standard IPX access lists, extended IPX
access lists, and SAP access lists.
Standard IPX Access Lists
When deciding what this book should really try to accomplish, I decided that the text of the
book should cover the topics in two ways. First, the voluminous details should be summarized
in tables and lists whenever possible, to allow easy review for a reader who already knows the
Routing
Logic
ACL
Permit
Permit
Router
Deny
IPX Packet
ACL
Bit
Bucket
Deny
Outbound
Inbound
ch07.fm Page 479 Monday, March 20, 2000 5:14 PM
