464 Chapter 7: Understanding Access List Security
The following example, illustrated by Figure 7-3, Example 7-1, and Example 7-2, shows a basic
use of standard IP access lists, with two typical oversights in the first attempt at a complete
answer. The criteria for the access list(s) is as follows:
·
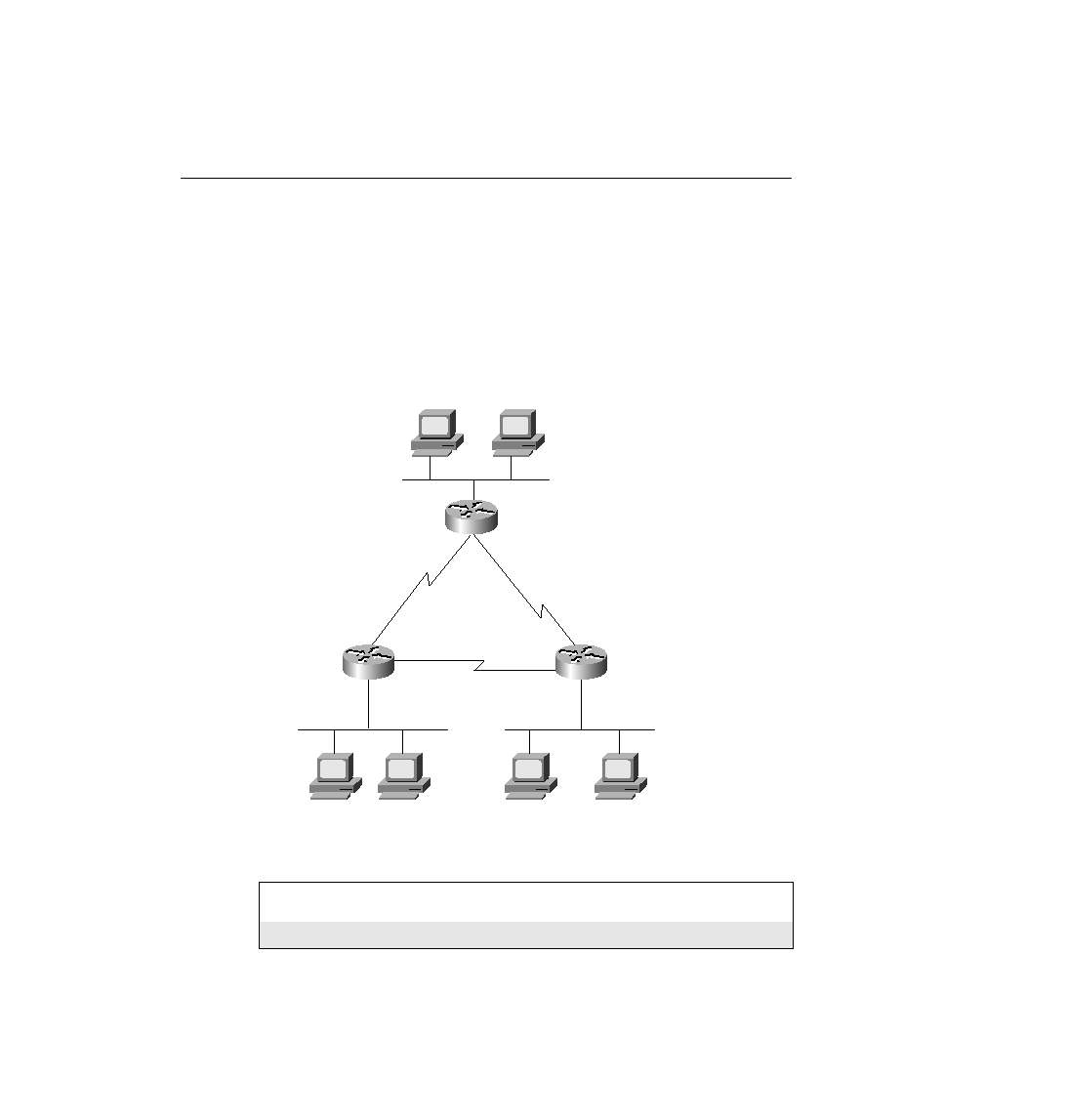
Sam is not allowed access to Bugs or Daffy.
·
Hosts on the Seville Ethernet are not allowed access to hosts on the Yosemite Ethernet.
·
All other combinations are allowed.
Figure 7-3
Network Diagram for Standard Access List Example
Example 7-1
Yosemite Configuration for Standard Access List Example
interface serial 0
ip access-group 3
!
access-list 3 deny host 10.1.2.1
access-list 3 permit any
Bugs
Sam
10.1.2.1
Emma
10.1.2.2
Elmer
Red
Daffy
Albuquerque
Seville
Yosemite
s1
s1
s1
s0
s0
s0
Subnet 10.1.130.0
Subnet 10.1.1.0
Subnet 10.1.128.0
Subnet 10.1.2.0
Subnet 10.1.3.0
Subnet 10.1.129.0
ch07.fm Page 464 Monday, March 20, 2000 5:14 PM

