|
|

To use Cisco Centri Firewall, you must determine what assets you want to protect, who you are protecting those assets from, who can access them, how they can be accessed, and who can change the rules about accessing them. In addition, you need to determine what information you want to know about your network's activity and what to do and who to notify if someone attacks your assets. The basic install and configuration process involves seven tasks:
1. Define your administrative accounts.
2. Set up your network objects.
3. Define your network services.
4. Define your user authentication policies.
5. Define your security policies.
6. Apply your security policies.
7. Set up reporting and monitoring.
This chapter provides an overview of these seven tasks and provides information to help you plan the deployment of your Cisco Centri Firewall, as well as worksheets for collecting and organizing the information about your network that you will need to know when configuring Cisco Centri Firewall. Detailed procedures for performing these tasks are provided in the HTML Reference documentation that is installed with the security system.
You must define at least one administrative account for Cisco Centri Firewall to allow privileged users to administer the security system. In addition, you must specify which Windows NT user account should be used to install Cisco Centri Firewall. This user account must have administrative privileges because the Cisco Centri Firewall must be able to run its services with administrative or system-level privileges.
During the installation process, you will be prompted to define your default administrative account for Cisco Centri Firewall. Once you install the product, you must consider additional accounts for administrators who need to administer the firewall from remote workstations (see Figure 6-1). To set up administrative accounts for Centri Firewall, you must determine who can administer your firewall server and from what computers on your network they can administer it. This process defines the remote administration privileges and user accounts.
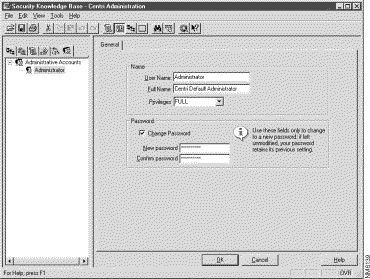
Once you have installed Cisco Centri Firewall, you need to set up your network by identifying the network objects that you want to protect, and possibly, those network objects that exist on untrusted networks that you want to allow your users to access while adhering to specific security policies.
Within Cisco Centri Firewall, trusted network objects are placed under the Network tree. Two types of trusted networks exist: physical networks and logical networks.
The physical relationships that you must define during the install process instruct the Cisco Centri Firewall about the proper flow of network traffic across the firewall server. The relationships include whether to hide or expose the internal site addresses (basic rules for network address translation) and what internal network servers you want to share with external network users. The physical relationships also define many physical characteristics of your network, such as:
By defining the physical relationships of your network, you can do more than define routing rules—you can define Windows NT domain controllers that allow you to apply security policies to the Group and User accounts within the user account databases on those domain controllers.
The Windows NT authentication model provides several benefits:
Defining the physical relationships involves three basic tasks:
The next section discusses how you can use logical relationships to simplify the administration of your network.
The logical relationships of your network allow you to administer it more efficiently, without worrying about the physical layout of your network. By defining logical network objects, you can group network objects that reside behind routers, as well as apply specific security polices to users and hosts that do not run Windows NT client operating systems (Windows NT Workstation, Windows 95, and Windows for Workgroups 3.x).
With physical network objects, you are more concerned about communicating with the first line of network objects, such as routers, to ensure that the firewall server directs traffic correctly. With logical network objects, your focus is on how you want to view and administer the network objects for the purpose of simplifying security policy deployment (see Figure 6-2). You can provide as much or as little detail about your network as needed to administer it in the manner that your security policy dictates.
For example, if you had a homogenous UNIX environment connected to your firewall server (either trusted or untrusted), you could mimic the domain model in which you commonly administer the UNIX workstations. You could represent this domain model as entire domains using subnetwork and IP address ranges, or you could represent the domains populated with every workstation within that domain. These two examples would allow you to apply security policies on a domain-only, a domain-workstation combination, or a workstation-only basis.
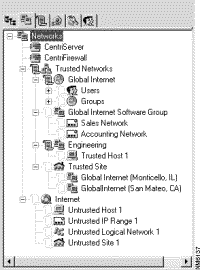
In addition, you could define user authentication requirements for each of these network objects to comply with corporate policy. If you are more comfortable with usernames, you can identify specific computers or networks using the names of your users or departments within your organization instead of using hostnames and domain names.
Once you determine the organizational model by which you want to administer your network, you must define the logical network objects and groups that reflect that model to the level of detail that you require.
To define new services so, simply select the network services and applications that you want to allow on your network and organized them into meaningful Bundled Applications (see Figure 6-3). Using Bundled Applications, you can organize network services and applications into a higher level object that you can reference in your security policies as a single entity.
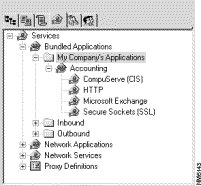
If the network services and network applications provided with the Cisco Centri Firewall do not fit your needs, you can also use the New Service Wizard to define new network services that you can also include in your custom Bundled Applications. To access this wizard, select the Network Services branch within the Services tree. On the shortcut menu (accessed using the right-mouse button), click the Service Wizard option from the New option (see Figure 6-4).
The network services wizard walks you through the process of defining a new network service based on the kernel proxies that compose the dynamic stack that will be used to evaluate sessions for that network service.
The last step required to set up your network services is to define the rules for HTTP filtering. Like other value-added services, such as ActiveX and Java filtering, you can specify the enforcement of these filtering rules on a per instance basis within security policies. Centri Firewall provides the ability to control which Internet sites are accessible to the users on your private network, as well as prevent access to specific types of files. To specify rules for the HTTP filtering service, select the Centri Server node under the Networks tree.
You can configure the FTP, Telnet, and HTTP network services to authorize specific external users to access your network. However, this open-ended access poses a threat to your network's security because malicious external users often attempt to penetrate a company's firewall by copying an authorized external user's transactions and then masquerading as that user. You can prevent this kind of attack by requiring authorized external users to prove that they are who they say they are before granting them access to your network. Cisco Centri Firewall's user authentication policies provide a means of enforcing this proof concept.
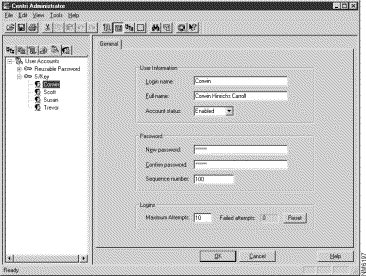
To define your user authentication policies, you must first determine whether you are going to require user authentication and if so, you must select the form of user authentication that you want to use: S/Key or reusable passwords. Once you have determined the need and authentication method, you must gather the information required by your users to authenticate themselves. Table 6-1 identifies the information that you will need to gather depending on which authentication method you choose.
| Authentication Field | Description |
Username | Identifies the account name that your network user will enter in conjunction with a password to authenticate himself to the firewall server. |
Full Name | Identifies the user's full name. This information helps you identify exactly who owns a particular user account. |
Status | Specifies whether the user account is enabled or disabled. Using this feature, you can define user accounts in advance and only enable them when the user requires access to the firewall server. This level of control reduces the risk of attackers compromising the user account. |
Passwords | Identifies the passwords that your network user will enter in conjunction with a user account to authenticate himself to the firewall server. |
Sequence Number | This option is used exclusively by the S/Key authentication method. It specifies how many times a user can log into the firewall server before the user account/password list must be updated. This number decrements each time the user logs in, and when it reaches zero, the account is automatically disabled by the firewall server. |
Maximum Attempts | Identifies the maximum number of attempts that a user can consecutively fail to log into this account before it is automatically disabled. You must reset disabled accounts manually. |
The last step of this task is to define the user accounts within the User Authentication tree of the Cisco Centri Firewall user interface. From within the User Accounts tree, you can define both reusable- and S/Key-based user authentication accounts. Once these accounts are defined, you can require that your network users authenticate themselves to the firewall server before accessing the HTTP, FTP, or Telnet services.User Authentication Methods.
Because many network services and applications perform bi-directional communications (both the client and server can initiate a session), you must define two types of security polices:
Outbound security policies specify which users and services, such as FTP and e-mail servers, on your trusted networks can communicate with users and services that reside on untrusted and unknown networks. Inbound security policies specify which users and services can communicate with the users and services that reside on your trusted networks.
For example, if you want your users to be able to send and deliver e-mail to users who reside on untrusted and unknown networks, you must specify an inbound security policy that allows SMTP-based messages (or a similar mail service) to reach your internal mail server. In addition, you must specify an outbound security policy that allows your internal mail server to deliver SMTP-based messages out to untrusted and unknown networks.
When defining your security polices, you must determine which network services, applications, and bundles you want to allow your logical network objects to access. You must also specify any run-time session controls that you want applied to specific network services, such as user authentication, ActiveX and Java filtering, and time-of-day access restrictions.
To enable bi-directional communication, you must apply the security polices to the appropriate network objects. To enable inbound communications, you must apply security policies that enable the allowed network services to the Internet branch or any children nodes that you have defined below it. By doing so, you are allowing network objects that are external to your network to communicate with internal network objects on your internal trusted networks.
To allow outbound communications, you simply apply the security policies that you defined for outbound communications to the logical network objects that you defined within the Trusted Networks branch of the Networks tree. Thus, you are allowing your internal network objects to use the specified network services and applications to communicate with external network objects.
Within Cisco Centri Firewall, reporting and monitoring are closely related because the information that is processed for reports and evaluated by the monitoring system is dependent upon the events that you decide to store in the Security Knowledge Base. Two concepts are central to both of these subsystems: audit events and event filtering.
Audit events generate audit records that explain what is happening within the security system. All components and agents within the security system have assigned audit events, and the audit records that these events generate provide the information that is used to generate reports and administrator notifications.
Event filtering determines whether a specific event will be stored in the audit records of the Security Knowledge Base and whether an administrator will be notified. It provides the ability to filter out audit records that you do not want to permanently store in the Security Knowledge Base. Thus, event filtering is based on what the administrator believes is important to monitor. Some administrators want to study detailed reports describing every audit event that occurred within the security system, while others are more interested in specific information about how the security system is operating.
The first step in setting up your reporting and monitoring is to determine which audit events you want to generate records for and how and when you want to notify someone on your staff if a particular audit event occurs. By doing so, you are defining the monitoring settings.
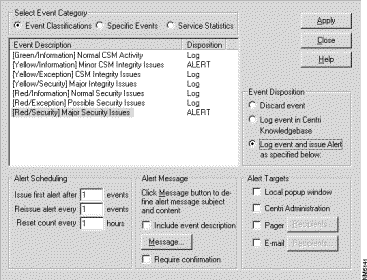
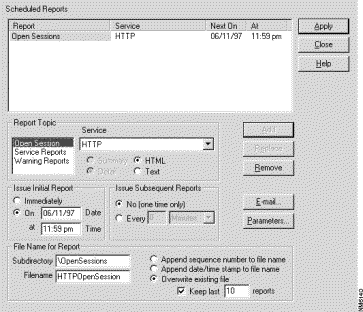
The last section of this chapter provides worksheets to help you organize and record information you will need as you configure Cisco Centri Firewall.
This section provides worksheets to help you configure Cisco Centri Firewall, as well as to plan and maintain your network security policy. We encourage you to copy these worksheets and to fill them out before you install and begin configuring Cisco Centri Firewall. The following worksheets are provided:
| IP Address | User/ Department | Importance (High/Low) | Network Applications | Network Services Required |
|---|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Network Object | ||||
| IP Address | Object Name | Importance (Low/High) | Notes | Type of Access Granted |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Sat Sep 28 22:53:25 PDT 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.