21. Firewalls
Contents:
What's a Firewall?
Building Your Own Firewall
Example: Cisco Systems Routers as Chokes
Setting Up the Gate
Special Considerations
Final Comments
Most systems for providing UNIX network security that we have discussed in this book are designed to protect an individual UNIX host from a hostile network. We have also explored systems such as Kerberos and Secure RPC , which allow a set of hosts to communicate securely in a hostile environment.
As an alternative to protecting individual computers on a network, many organizations have opted for a seemingly simpler solution: protecting an organization's internal network from external attack.
The simplest way to protect a network of computers is with physical isolation . Avoid the problems of networks by not connecting your host to the Internet and not providing dial-in modems. Nobody from the outside will be able to attack your computers without first entering your physical premises. Although this approach completely ignores the damage that insiders can do, it is nevertheless a simple, straightforward policy that has been used by most organizations for years. In many environments, this is still the best way to approach network security - there is little to be gained from connection to outside networks, and much to lose.
Recently, however, the growth of the Internet has made physical isolation more difficult. Employees in organizations want email, they want access to Usenet news, and they want to browse the World Wide Web. In addition, organizations want to publish information about themselves on the Web. To allow partial connection to the Internet, while retaining some amount of isolation, some organizations are using firewalls to protect their security.
Firewalls are powerful tools, but they should never be used instead of other security measures. They should only be used in addition to such measures.
21.1 What's a Firewall?
A firewall gives organizations a way to create a middle ground between networks that are completely isolated from external networks, such as the Internet, and those that are completely connected. Placed between an organization's internal network and the external network, the firewall provides a simple way to control the amount and kinds of traffic that will pass between the two.
The term firewall comes from the construction industry. When apartment houses or office buildings are built, they are often equipped with firewalls - specially constructed walls that are resistant to fire. If a fire should start in the building, it may burn out of control in one portion, but the firewall will stop or slow the progress of the fire until help arrives.
The same philosophy can be applied to the protection of local area networks of machines from outside attack. Used within an organization, a firewall can limit the amount of damage: an intruder may break into one set of machines, but the firewall will protect others. Erected between an organizational network and the Internet at large, a firewall prevents a malicious attacker who has gained control of computers outside the organization's walls from gaining a foothold on the inside. Firewalls seem to make sense because there is always a "fire" burning somewhere on the Internet.
21.1.1 Default Permit vs. Default Deny
The fundamental function of a firewall is to restrict the flow of information between two networks. To set up your firewall, you must therefore define what kinds of data pass and what kinds are blocked. This is called defining your firewall's policy . After a policy is defined, you must then create the actual mechanisms that implement that policy.
There are two basic strategies for defining firewall policy:
- Default permit
-
With this strategy, you give the firewall the set of conditions that will result in data being blocked. Any host or protocol that is not covered by your policy will be passed by default.
- Default deny
-
With this strategy, you describe the specific protocols that should be allowed to cross through the firewall, and the specific hosts that may pass data and be contacted. The rest are denied.
There are advantages and disadvantages to both default permit and default deny. The primary advantage of default permit is that it is easier to configure: you simply block out the protocols that are "too dangerous," and rely on your awareness to block new dangerous protocols as they are developed (or discovered). With default deny, you simply enable protocols as they are requested by your users or management. Any protocol that isn't being used by your organization might as well be blocked.
Neither default permit nor default deny is a panacea. With both policies, you can create a firewall that is either secure or unsecure, by permitting (or failing to deny) "dangerous" protocols.
21.1.2 Uses of Firewalls
Firewalls are part of a good defense in depth strategy. The idea is to place several layers of protection between your machines and the potential threats. There are some obvious threats from the outside, so you should naturally place a firewall between the outside and your internal network(s).
Because a firewall is placed at the intersection of two networks, it can be used for many other purposes besides simply controlling access. For example:
-
Firewalls can be used to block access to particular sites on the Internet, or to prevent certain users or machines from accessing certain servers or services.
-
A firewall can be used to monitor communications between your internal network and an external network. For example, you could use the firewall to log the endpoints and amount of data sent over every TCP/IP connection between your organization and the outside world.
-
A firewall can even be used to eavesdrop and record all communications between your internal network and the outside world. A 56KB leased line at 100% utilization passes only 605 MB/day, meaning that a week's worth of Internet traffic can easily fit on a single 8mm digital tape. Such records can be invaluable for tracking down network penetrations or detecting internal subversion.[1]
[1] Such records also pose profound privacy questions, and possibly legal ones as well. Investigate these questions carefully before engaging in such monitoring.
-
If your organization has more than one physical location and you have a firewall for each location, you can program the firewalls to automatically encrypt packets that are sent over the network between them. In this way, you can use the Internet as your own private wide area network ( WAN ) without compromising the data; this process is often referred to as creating a virtual private network , or VPN . (You will still be vulnerable to traffic analysis and denial of service attacks, however.)
21.1.3 Anatomy of a Firewall
Fundamentally, all firewalls consist of the following two kinds of components:[2]
[2] The first edition of this book introduced this terminology as part of one of the first written descriptions of firewalls. Although not everyone in the community has adopted these terms, we believe that they are at least as descriptive as other terms invented since.
- Chokes
-
Computer or communications devices that restrict the free flow of packets between networks. Chokes are often implemented with routers, but they do not have to be. The use of the word "choke" is taken from the field of electronics: a choke is a device that exhibits great resistance to certain types of signals, but not to others.
- Gates
-
Specially designated programs, devices, or computers within the firewall's perimeter that receive connections from external networks and handle them appropriately. Other texts on firewalls sometimes refer to single machines that handle all gate functions as bastion hosts.
Ideally, users should not have accounts on a gate computer. This restriction helps improve the computer's reliability and users' security.
On the gate(s), you may run one or more of the following kinds of programs:
- Network client software
-
Client software includes programs such as telnet , ftp and mosaic . One of the simplest ways to give users limited access to the Internet is to allow them to log onto the gate machine and allow them to run network client software directly. This technique has the disadvantage that you must either create user accounts on the gate computer, or you must have users share a single account.
- Proxy server
-
A proxy is a program that poses as another. In the case of a firewall, a proxy is a program that forwards a request through your firewall, from the internal network to the external one.
- Network servers
-
You can also run network servers on your gate. For example, you might want to run an SMTP server such as sendmail or smap so that you can receive electronic mail. (If you wish to run an HTTP server to publish information on the World Wide Web, that server should be run on a separate computer, and not on your gate.)
Many network servers can also function as proxies. They can do so because they implement simple store-and-forward models, allowing them to forward queries or messages that they cannot handle themselves. Some servers that can operate easily as proxies include SMTP (because email messages are automatically forwarded), NNTP (news is cached locally), NTP (time is maintained locally), and DNS (host addresses are locally cached). The following sections explore a variety of different kinds of firewall configurations in use today.
21.1.4 Dual-ported Host: The First Firewalls
The first Internet firewalls were UNIX computers equipped with two network ports: one for the internal network, and one for the external network (see Figure 21.1 ).
Figure 21.1: Firewall built from a dual-ported host
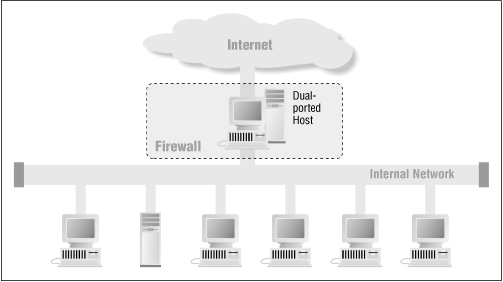
In this configuration, the UNIX computer functions as both the choke and the gate. Services are provided to internal users in one of two ways:
-
Users can log onto the dual-ported host directly (not a good idea, because users can then compromise the security of the firewall computer).
-
The dual-ported host can run proxy servers for the individual services that you wish to pass across the firewall.
To ensure that the computer functions as a choke, the computer must not forward packets from the external network to the internal network and vice versa. On most UNIX systems using Berkeley-derived TCP/IP , you can do so by setting the kernel variable ip_forwarding to 0.[3] Unfortunately, some UNIX systems will still forward packets that have IP source-routing options set. Thus, you should carefully examine any dual-ported UNIX system that is used as a choke to make sure that it will not forward packets from one interface to another.
[3] This setting is usually established with a SET in the /etc/system file under SVR4, or with a small shell and adb script under other systems. See your system documentation for details.
On a Solaris machine, you can disable both IP forwarding and forwarding of source-routed packets by including the following commands in some start-up file (e.g., in the appropriate file in /etc/rc2.d ):[4]
[4] Be careful when you set these variables. The file /etc/init.d/netinit (linked to /etc/rc2.d/S69inet) also contains explicit settings of the ip_forward variable. To avoid having your values overwritten, comment out the system code in inet that sets ip_forward , and put your code in its place.
ndd -set /dev/ip ip_forwarding 0 ndd -set /dev/ip ip_forward_src_routed 0
Note that under SunOS, you need to set ip_forwarding = 0 in the kernel configuration. If you don't, the kernel will still IP forward under some conditions even if you've set the ip_forwarding variable to 0.
21.1.5 Packet Filtering: A Simple Firewall with Only a Choke
A simple firewall can be built from a single choke (see Figure 21.2 .) For example, some organizations use the packet filtering features available on some routers to block the TCP and UDP packets for certain kinds of services.
Figure 21.2: Firewall built from a single choke
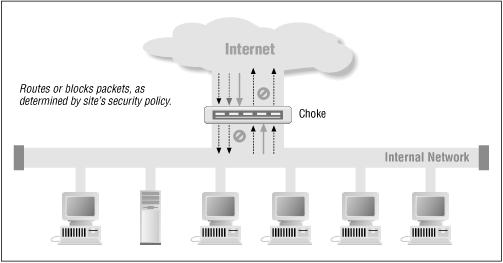
Programming the choke is straightforward:
-
Block all packets for services that are not used.
-
Block all packets that explicitly set IP source-routing options.
-
Allow incoming TCP connections to your predetermined network servers, but block all others.
-
Optionally, allow computers within your organization's network to initiate outgoing TCP connections to any computer on the Internet.
This is a simple configuration very popular on today's Internet. Many organizations use a single choke (usually a router) as a firewall for the entire organization.
Packet filtering has a number of advantages:
-
It is simple and cheap. Most organizations can build packet filters using routers that they already use to connect their networks to the Internet.
-
Packet filtering is flexible. For example, if you discover that a person on a particular subnet, say 204.17.191.0, is trying to break into your computer, you can simply block all access to your network from that subnet. (Of course, this method will only work until the user at the subnet decides to launch an attack against you from another network or begins to forge IP addresses in the packets.)
Packet filters have several disadvantages:
-
Filters typically do not have very sophisticated systems for logging the amount of traffic that has crossed the firewall, logging break-in attempts, or giving different kinds of access to different users; however, some routers now include support for logging filter violations through the use of syslog .
-
Filter rulesets can be very complex - so complex that you might not know if they are correct or not.
-
There is no easy way to test filters except through direct experimentation, which may prove problematical in many situations.
-
Packet filters do not handle the FTP protocol well because data transfers occur over high-numbered TCP ports; however, this problem can be alleviated by FTP clients that support the FTP passive mode.
In addition to these disadvantages, there are several fundamental design weaknesses with packet filters:
-
If the security of the router is compromised, then all hosts on the internal network are wide open to attack.
-
You may not know if the security of the router is compromised because there is no simple way to test the router's configuration tables.
-
Although the router may record the number of packets that are passed and blocked, it usually does not record other kinds of useful information.
-
The router may allow remote administration. It may not alert you if somebody is repeatedly trying to guess its access password.
-
The scheme can easily be defeated with minimal aid from a cooperative (or duped) insider.
-
There is no protection against the contents of some connections, such as email or FTP transfer contents.
21.1.6 One Choke, One Gate: Screened Host Architecture
You can build a more secure firewall using a choke and a gate. The gate is a specially chosen computer on your network at which you run your mail server and any user proxy programs. ( WWW servers and anonymous FTP servers should be run on separate computers, outside the firewall.) The choke can be a router with two interfaces. For example, a router with two Ethernet interfaces can partition one network from another. Alternatively, a router with an Ethernet and a high-speed interface can serve both as a gate and as an organization's connection with an off-site Internet service provider ( ISP ).[5] (See Figure 21.3 .)
[5] Many ISPs will, as a courtesy, maintain the router that connects your network to theirs. If you allow your ISP to maintain your router, then you should not use it as the basis for your firewall. Instead, you should have a second router behind the first router that is used only for security.
Figure 21.3: Traditional firewall with a choke and a gate
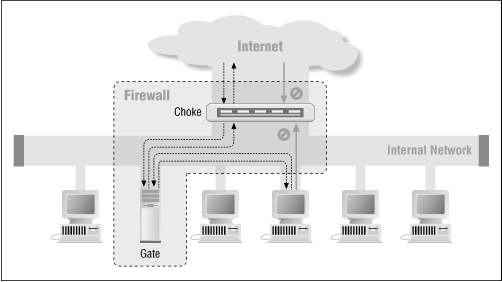
Programming is somewhat more complex in this arrangement.
External choke:
-
Block packets for services that you do not wish to cross your firewall.
-
Block packets that have IP source routing, or that have other "unusual" options set (e.g., record-route).
-
Block packets that have your internal network as their destination.
-
Only pass packets for which the source or destination IP address is the IP address of the gate.
Gate:
-
Runs server proxies to allow users on the inside network to use services on the external network.
-
Either acts as a mail server, or receives mail from the external network and forwards it to a specially designed host on the internal network.
With this configuration, the choke is configured so that it will only pass packets between the outside network and the gate. If any computer on your inside network wishes to communicate with the outside, the communication package must pass through a special "proxy" program running on the gate.[6] Users on the outside network must connect to the gate before bridging through to your internal network.
[6] We describe one such set of proxies in Chapter 22, Wrappers and Proxies .
21.1.7 Two Chokes and One Gate: Screened Subnet Architecture
For a higher degree of security, some sites have implemented a firewall built from two chokes, as shown in Figure 21.4 .
Figure 21.4: . Firewall built from two chokes and one gate
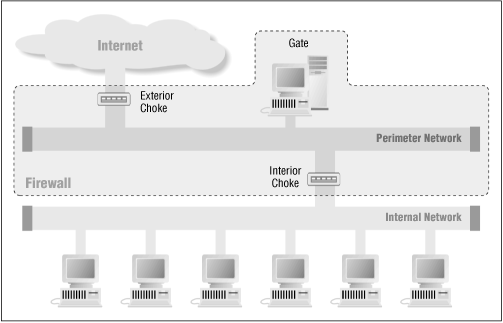
In this configuration, both the external choke and the gate are programmed as before. What's new is the addition of an internal choke. This second choke is a fail-safe: in the event that an attacker breaks into the gate and gains control over it, the internal choke prevents the attacker from using the gate to launch attacks against other computers inside the organization's network.
Programming is similar to that of a single choke:
External choke:
-
Block packets for services that you do not wish to cross your firewall.
-
Block packets that have IP source routing or that have other "unusual" options set.
-
Block packets addressed to your internal network or your internal choke.
-
Only pass packets for which the source or the destination IP address is that of the gate.
Gate:
-
Runs server proxies to allow users on the inside network to use services on the external network.
-
Either acts as a mail server, or sends mail to a specially designed host on the internal network.
Internal choke:
-
Block packets for services that you do not wish to cross your firewall.
-
Block packets that have IP source routing or that have other "unusual" options set.
-
Block packets addressed to the external choke.
-
Pass packets for which the source or destination IP address is that of the gate, and for which the ports are for defined proxies on the gate.
-
Block everything else.
21.1.8 Multiple Gates
Instead of using a single gate, you can use several gates - one for each protocol. This approach has the advantage of making the gates easier to administer. However, this approach also increases the number of machines that must be carefully watched for unusual activity. A simpler approach might be to have a single gate, but to create individual servers within your organization's network for specific services such as mail, Usenet, World Wide Web, and so forth.
21.1.9 Internal Firewalls
Instead of putting all your organization's machines on a single local network, you can separate your installation into sets of independent local area networks. These networks can communicate through gateway machines, routers, or full-blown firewalls. Alternatively, they can communicate with each other through independent links to the Internet, using an appropriate encryption system to prevent eavesdropping by your ISP and others.
Internal firewalls make a lot of sense in a large organization. After all, there is no reason to allow your research scientists any privileged access to a computer that is used for accounting, or to allow people who are sitting in front of data-entry terminals to try their hand at breaking into the research and development department's file servers. With an internal firewall, you can place extra security where needed.
The goal in setting up independent internal networks should be to minimize the damage that will take place if one of your internal networks is compromised, either by an intruder or, more likely, by an insider. By practicing stringent isolation, you can reduce the chances that an attacker will be able to use a foothold in one network as a beachhead for breaking into others.
A firewall designed for use within an organization is very similar to one that is used to protect an organization against external threats. However, because the same management team and structure may be responsible for many networks within an organization, there is a great temptation to share information or services via an internal firewall, when such information services should in fact be blocked.
Follow these basic guidelines when setting up independent internal networks:
-
If you use NIS , make sure that each local area network has its own server. Make sure that each server and its clients have their own netgroup domain.
-
Don't let any server or workstation on one network trust hosts on any other network or any gateway machine. (For an explanation of trusted hosts, see "Trusted hosts and users" in Chapter 17, TCP/IP Services .)
-
Make certain that users who have accounts on more than one local network have different passwords for each subnet. If possible, use a one-time password scheme or token-based system.
-
Enable the highest level of logging for the gateways, and the most restrictive security possible. If possible, do not allow user accounts on the gateway machines.
-
Do not NFS -mount filesystems from one LAN onto another LAN . If you absolutely must share a partition, be sure that it is exported read-only.
Internal firewall machines have many benefits:
-
They help isolate physical failure of the network to a smaller number of machines.
-
They limit the number of machines putting information on any physical segment of the network, thus limiting the damage that can be done by eavesdropping.
-
They limit the number of machines that will be affected by flooding attacks.
-
They create barriers for attackers, both external and internal, who are trying to attack specific machines at a particular installation.
Remember: Although most people spend considerable time and money protecting against attacks from outsiders, dishonest and disgruntled employees are in a position to do much more damage to your organization. Properly configured internal firewalls help limit the amount of damage that an insider can do.
In the following text, we'll refer to internal networks and external networks when describing a firewall, with the understanding that both networks may in fact be internal to your organization.




