
| Previous | Table of Contents | Next |
CISCO INTERNETWORK DESIGN EXAM OBJECTIVES COVERED IN THIS CHAPTER:
As touched upon in Chapter 1, security is a component of network design that overshadows every other facet of the network. Thus, it is imperative to consider data security from the onset of any design. While it is possible to add security to a strong network design, this tactic typically incorporates compromises. These compromises start with the security model itself and ultimately lead to significant changes in the overall network design.
Since every network is different, it is up to each designer to evaluate the security needs of their own networks. Also important to consider are the network’s interrelationships with other components, including routing protocols, operating systems, and physical security. Physical security is as important as the logical components designers typically consider—the best access list is void if the hacker can physically access the router, for example.
Primarily, this chapter focuses on the generic, conceptual level of network security. Don’t make the mistake of considering this chapter a comprehensive dissertation on the subject. It would be easy to compose a complete text on network security, and many authors have. Yet for the exam, this presentation provides sufficient information and yields some additional elements to help apply this material in a production network. For example, one specific area that warrants more treatment than is required for the CID exam is interoperability between firewalls and Cisco routers. Readers may wish to explore the issues surrounding this topic and consider how it applies to the Cisco-centric view. For instance, most firewalls do not support EIGRP. This automatically results in a requirement to use static routes or a redistribution of EIGRP into a more universally supported routing protocol—typically RIP or OSPF. This fact could significantly alter a security design.
 | The majority of this text addresses the concept of TCP/IP security, which clearly does not present a complete security solution. However, many of the ideas presented herein are applicable to the broader demands of data protection. |
In order to understand the data security component of networking, it is important to view threats to the network as internal or external. An internal threat is one that uses privileged information to gain access from the outside or an attack that starts from an internal, trusted network. An external threat is one that uses an untrusted access point, such as the Internet, to gain access to the corporate network.
 | Some attacks may use a combination of internal and external means to gain access to data. For example, a fired employee may use his internal knowledge of the network to gain access via an outside connection. According to security experts, most attacks involve at least some inside information or access. |
Corporations must realize that data security is an interesting legal problem. Many countries have not developed adequate regulations to make hacking a crime. Unfortunately, this results in little recourse when an attack is successful. While the legal system is catching up to the incredible pace of change, it is preferable to prevent as many attacks as possible and to capture as much information as possible.
 | This text uses “hacking” in a generic context to encompass all types of unauthorized entry into computer systems, including phreaking (phone hacking) and cracking. |
All security models must start with a policy—a statement of what will and will not be permitted within the network. The best way to approach this is with a security document that clearly spells out the terms of the policy. This may be very detailed, spelling out each and every element of the policy, or it may be intentionally vague, simply framing the general authorizations. Unfortunately, few organizations actually take the time to compose such a document, and when it is written, it remains fairly static—meaning that it outlines a historical policy, rather than one that keeps up with the everchanging landscape.
As if the lack of documentation wasn’t discouraging enough, many architects and managers find that the senior business management will not sign even the most basic of security documents. This typically results from fear— either a lack of understanding or the desire to not take responsibility should the network be compromised. This places any and all technical solutions at grave risk.
When the business has not predefined the expectations of the security solution, it cannot succeed. In addition, each time a specific business desires to add new services, there will need to be a new evaluation of the request and risk—a time-consuming and politically charged proposition.
Rather than dwell on the importance of good company politics in security designs, this section addresses other single points in perimeter protection, including:
In addition to physical security, complete security models must also include server and workstation operating system security. This chapter approaches this with discussions of encryption, host security, and authentication and authorization.
Perimeter security, establishing a border around the trusted network, typically uses a firewall to thwart attacks. The purpose of the firewall is to implement policy and provide the administrator with a single point from which to control access. An important consideration for the designer is to not make this a single point-of-failure in the installation. Figure 11.1 illustrates a typical, single-system firewall deployment. In this case, the firewall actually uses two components—the router and a distinct firewall device (the Cisco PIX, which is discussed in detail later in this chapter).
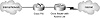
FIGURE 11.1 A simple firewall deployment
While the perimeter devices shown in Figure 11.1 include only a router and a firewall, production installations generally include some or all of the following:
| Previous | Table of Contents | Next |